-
Uncovering a Critical Authentication Vulnerability in Qwen AI
- February 9, 2025
- Posted by: Bikash Sharma
- Category: Awareness, Case Study
No Comments
-
“Blood on the Floor” – The Aftermath of Critical Security Breaches: A Wake-Up Call for Businesses
- January 28, 2025
- Posted by: Bikash Sharma
- Category: Awareness, Business plans, Business plans, Case Study
-
How Our VAPT Services Identify Hidden Vulnerabilities
- December 12, 2024
- Posted by: Bikash Sharma
- Category: Awareness, Business plans, Case Study
-
Everything about DDoS Attack
- May 31, 2022
- Posted by: Admin
- Category: Case Study, Competitive research
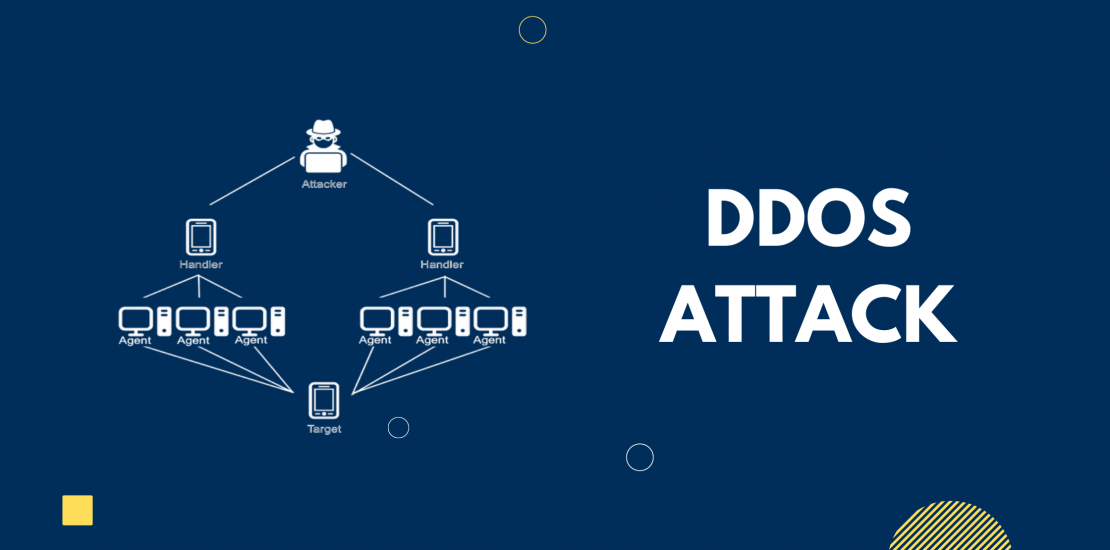
DDoS is an abbreviation for Distributed Denial of Service. An assault on the service or network is launched with the intent of interrupting regular functioning. Hackers bombard the victim with continual traffic, such as HTTP floods, Ping floods, fake requests, and so on.
-
Keep sensitive data out of logs with these five recommended security log practices.
- May 16, 2022
- Posted by: Admin
- Category: Case Study, News, Research

Because security and privacy are intertwined, you must develop the practice of safeguarding both. It may appear to be a time-consuming and daunting task, but understanding the interconnection between the terms helps businesses to maintain customers’ trust and use data to make a positive impact.
-
The Difference: Data Privacy vs. Data Security
- May 2, 2022
- Posted by: Admin
- Category: Case Study, News, Research

Because security and privacy are intertwined, you must develop the practice of safeguarding both. It may appear to be a time-consuming and daunting task, but understanding the interconnection between the terms helps businesses to maintain customers’ trust and use data to make a positive impact.
-
Cybersecurity Transformation: Unlocking Innovation, Brand Growth
- April 8, 2022
- Posted by: Admin
- Category: Case Study, News

How much risk can a business take in terms of staying both competitive and dependable to its customers? Isn’t it true that every company’s primary endpoint is to earn trust? It’s the best long-term competitive edge a company can have. A flawless cybersecurity strategy should not be overlooked if you want to be or become a consistently profitable, future-proof, and competitive business.
-
The battle of digital privacy, lapsus$ scandalous data breach on Microsoft, Samsung, Okta, Nvidia.
- April 4, 2022
- Posted by: Cynical_Technology
- Category: Case Study, News

An alarming data breach! All about Lapsus$ attack on Microsoft, Samsung, Okta, Nvidia. Here’s how to safeguard your information |Cynical Technology
-
RedLine: Malware Insights
- March 15, 2022
- Posted by: Admin
- Category: Case Study, Malwares

RedLine Stealer is the newly emerging stealer or malware that is targeting Windows users. This collects users’ information and delivers malicious programs.
