- March 15, 2022
- Posted by: Admin
- Category: Case Study, Malwares

Introduction
RedLine Stealer or RedLine is the newly emerging stealer or malware that is mainly targeting Windows users. This malware can collect information about the users and deliver other malicious programs. Basically, victim credentials and cryptocurrency wallets, as well as Browser information, FTP connections, game chat launchers, and OS information such as system hardware, processes names, time zone, IP, geolocation information, OS version, and default language are collected.
Description
RedLine Stealer appeared in March 2020 and has gained the stream through various channels. It was at its peak during COVID-19 and is still active. It actually spread as popular services like telegram, Signal, Discord, etc. (i.e. legit-looking installers), email phishing campaigns, abusing Google Ads, etc. Redline stealer is also known as infostealer whose main target is to steal the information about the users from the browser, system instant messaging, passwords, credit card information, username, location, autofill data, cookies, software set, and even hardware configuration like keyboard layout, UAC settings, etc. Recently, an update of this infostealer is also capable of stealing cryptocurrency.
RedLine malware is written in C# and uses a SOAP API to establish communication with the C2 server. This malware takes the feature of telegram API to notify the attackers in an easy way.
Below is the time format for the rapid release of RedLine malware.
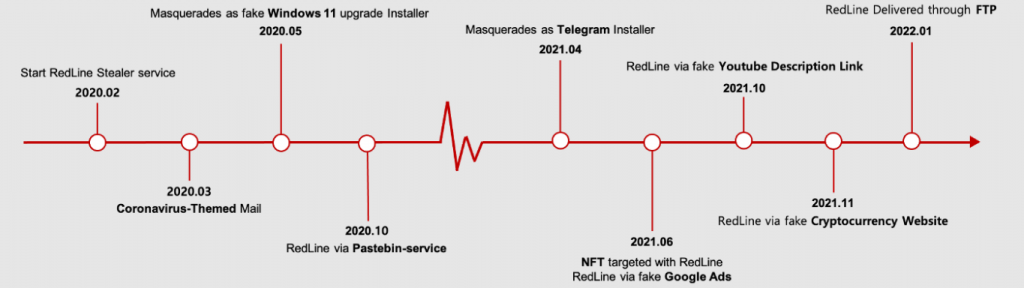
Technical Analysis
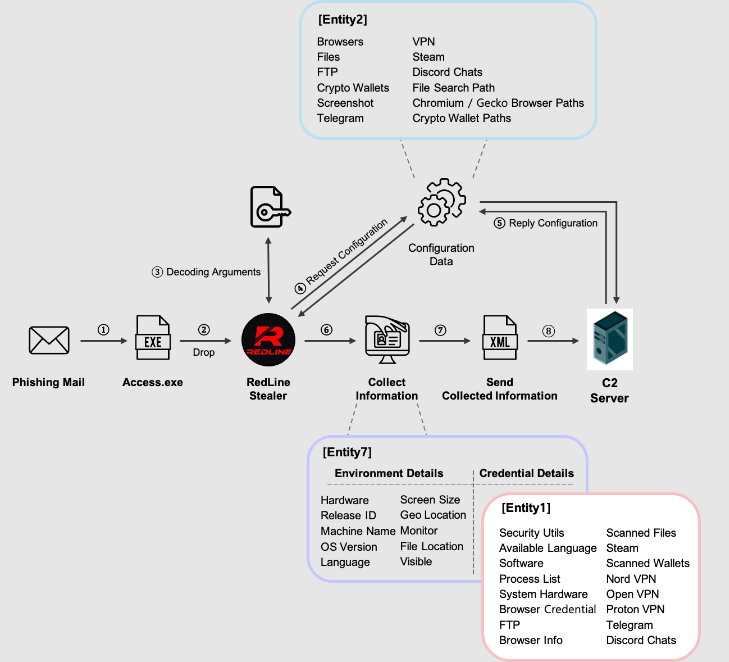
In order to execute the RedLine Malware, at first, the user will be emailed with the attachment of cracked software or the user will download cracked software from the websites with Redline Stealer inside. When cracked software is executed, Redline is also executed in the background. Then, encoded data such as C2 Server IP and Unique ID are decoded along with the XOR key and used for C2 communication.
After finishing the decoding process, the Redline stealer will request the configuration data from C2 Server, only if there is the availability of connection. Then, malicious users try to obtain Scan Settings i.e. information to be stolen from an infected PC. After this, information is collected based on the Scan Settings i.e. structure that stores the configuration data. After everything is stolen, the stealer just quits.
Finally, information that is leaked from the infected PC is as given below.
- Files: Any specified files in the following directories: ProgramData, Program Files, Program Files (x86).
- Browsers: Login credentials, Cookies, Auto-fill fields used by websites, and Credit card details.
- Crypto Wallets: Credentials of Armory, Exodus, Ethereum, Monero, Atomic, BinanceChain, and a lot more.
- VPN Clients: Credentials of the following VPN clients: NordVPN, ProtonVPN, and OpenVPN.
- Gaming Clients: It’s targeting the credentials of the famous Valve’s Steam gaming platform.
- Instant Messengers: Currently it’s targeting Telegram session data and Discord tokens.
- FTP Clients: Credentials of FileZilla FTP client.
After collecting all the information it is converted into XML format and transmitted to the C2 Server through SOAP Message.
Below you can see the work execution of RedLine Malware.
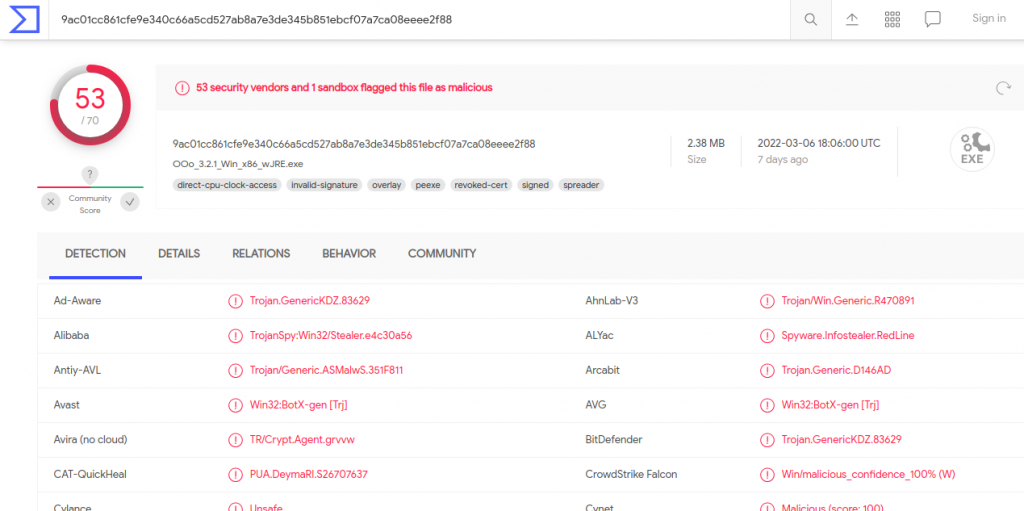
As you can see in the below figure, about 53 vendors have been flagged as malicious according to the VirusTotal. If you would like to see this in more detail this just visit VirusTotal.
You can see the format in which data is leaked on the dark web.
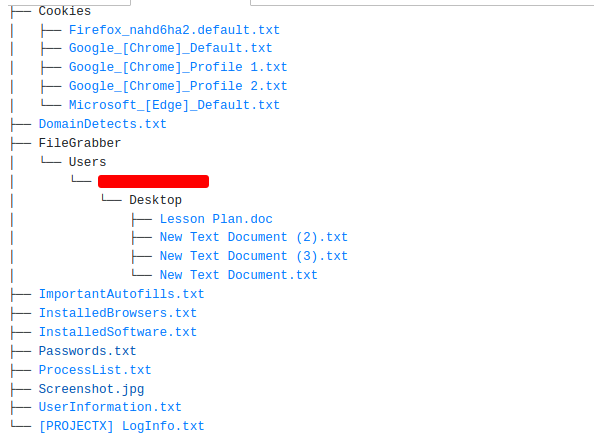
Distribution
We can notice the big variety of file formats here:
- Office
- RAR and ZIP
- Executable files( cracked software:- AutoCAD, KMSpico, Fifa, Adobe product, Bluestack, etc)
- JavaScript
Below is the latest distribution of Redline malware in any.run along with some screenshot
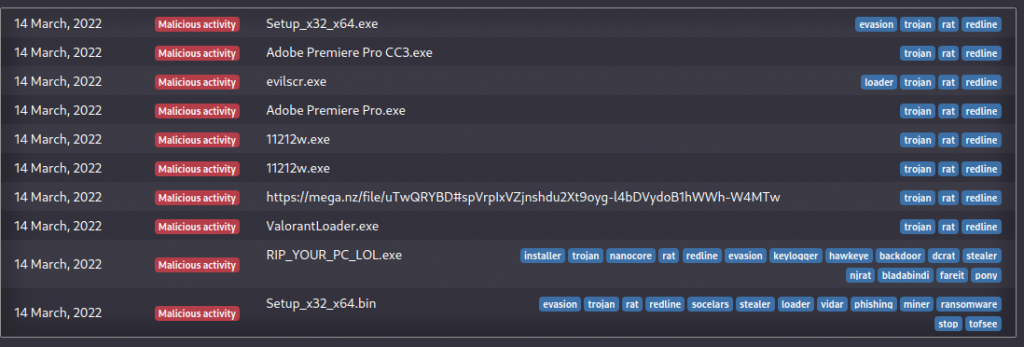
How to Stay Safe from Malware
Things you have to consider so that you will not be a victim of any malware: –
- Update your Operating System and scan with legitimate antivirus daily.
- Software and files should not be downloaded or installed through third party downloaders
- Installed software must be updated and activated through tools or functions that are designed by official developers.
- Avoid using Cracked software.
Conclusion
RedLine threats will not fade away in the very near future. So, the best way to protect organizations or devices from RedLine malware is to make employee security awareness training so that they can identify and be suspicious of unsolicited emails and phishing campaigns, unusual communications via social media, especially messages with embedded links or file attachments that could lead to the deployment of additional malicious payloads.
IoCs
The following samples were observed in 2021 and may be beneficial for those seeking to further understand the nature of this threat:
- f224b56301de1b40dd9929e88dacc5f0519723570c822f8ed5971da3e2b88200
- ffee20e0c17936875243ac105258abcf77e70001a0e8adc80aedbc5cfa9a7660
- 88ff40bd93793556764e79cbf7606d4448e935ad5ba53eb9ee6849550d4cba7f
- 6be3a52cd5c077794a03f0596d1cbf3aee2635d268b03b476f6a2eaeb87d411c
- 0ddd7d646dfb1a2220c5b3827c8190f7ab8d7398bbc2c612a34846a0d38fb32b
- 5df956f08d6ad0559efcdb7b7a59b2f3b95dee9e2aa6b76602c46e2aba855eff
References
- https://medium.com/s2wblog/deep-analysis-of-redline-stealer-leaked-credential-with-wcf-7b31901da904
- https://cyberint.com/blog/research/redline-stealer/
- https://www.proofpoint.com/us/blog/threat-insight/new-redline-stealer-distributed-using-coronavirus-themed-email-campaign
- https://malpedia.caad.fkie.fraunhofer.de/details/win.redline_stealer
