- May 16, 2022
- Posted by: Admin
- Category: Case Study, News, Research

Creative criminal minds around the world are manipulating these sophisticated latest technologies or the devices connected to the internet. Professional hackers are constantly battling criminals to protect computers, networks, programs, data, and, most importantly, people from unauthorized access, manipulations, exploitations, and attacks intended at causing harm in any way.
The greater the number of network devices in your network, the greater the risk of security vulnerabilities arising from insufficient log monitoring. There are several best practices you can use to ensure security log integrity; the article will show you the security log best practices.
Login security is still an uncharted area for many firms that receive little attention. It’s no surprise that security professionals and leaders emphasize the virtues of a safe and optimized login procedure, not only for consumers but also for maintaining business trust.
Here are a few of the best login security practices that every organization should follow.
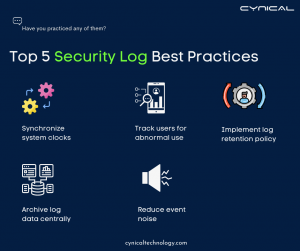
- Synchronize system clocks; The clocks on all systems should be synced in order for security log entries to have accurate time stamps throughout retention. Even a little time difference can make reconstructing the chain of events that led to a security breach much more difficult. By checking and correcting any massive differences in your system clocks on a frequent basis, you may reduce the chances of security incidents remaining unreported.
- Track users for abnormal use; Monitoring endpoint log activity is critical for determining how many people are operating on which devices for how long. Endpoint use tracking also allows you to track user behavior such as logins, file access, and remote-control events (if enabled), which can help you figure out who might be behind the unusual performance.
- Implement log retention policy: When opposed to other log formats, such as application log data, security logs should be kept for longer periods of time because they serve as evidence against data breaches and attacks. However, you can’t keep them indefinitely. To keep the relevant log data and erase the older data, log retention policies must be set up.
- Archive log data centrally; For regulatory compliance, centrally archiving all logs and verifying their integrity is critical. Ensure that you encrypt these logs while archiving, and implement time stamping, hashing, and other measures to keep the data safe.
- Reduce event noise; When you log too many events, it’s tough to discover the ones that matter during retention. To maintain compliance with regulations and network security, carefully configure your audit policies to log crucial events such as logon failures, account lockouts, and file access.
Summary
The security posture and safeguards of your logging system tend to be much laxer than a database that stores sensitive data. It’s not uncommon (especially in a startup) for the entire company to have access and tools to query that data. These best practices can put you on the right path to keeping sensitive data out of logs.
