- December 12, 2024
- Posted by: Bikash Sharma
- Category: Awareness, Business plans, Case Study
How Our VAPT Services Identify Hidden Vulnerabilities
In today’s fast-paced digital landscape, ensuring the security of your organization’s digital assets has never been more critical. With cyber threats evolving rapidly, vulnerabilities in your systems can become potential entry points for malicious attackers. To stay ahead of these threats, organizations need a proactive approach to identify and address weaknesses before they can be exploited. This is where Vulnerability Assessment and Penetration Testing (VAPT) services play a pivotal role.
In this blog post, we’ll dive deep into how our VAPT services uncover hidden vulnerabilities, what the process entails, and why it is essential for safeguarding your business.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security evaluation process that combines two critical methodologies:
- Vulnerability Assessment (VA): A systematic process to identify, classify, and prioritize vulnerabilities in a system.
- Penetration Testing (PT): Simulating real-world attacks to exploit vulnerabilities and evaluate the system’s security posture.
Together, these approaches provide a thorough understanding of potential weaknesses and their impact on your organization’s security.
Why VAPT is Essential
1. Prevent Data Breaches
Data breaches can cause significant financial and reputational damage. Identifying and fixing vulnerabilities early can prevent unauthorized access to sensitive data.
2. Meet Compliance Requirements
Many industries require regular security assessments to meet regulatory standards such as GDPR, HIPAA, and PCI DSS. VAPT helps ensure your organization remains compliant.
3. Protect Business Reputation
A security breach can damage customer trust and your company’s reputation. Proactive security measures help maintain your credibility.
4. Understand Your Risk Profile
VAPT provides insights into your organization’s security posture and highlights areas that need improvement.
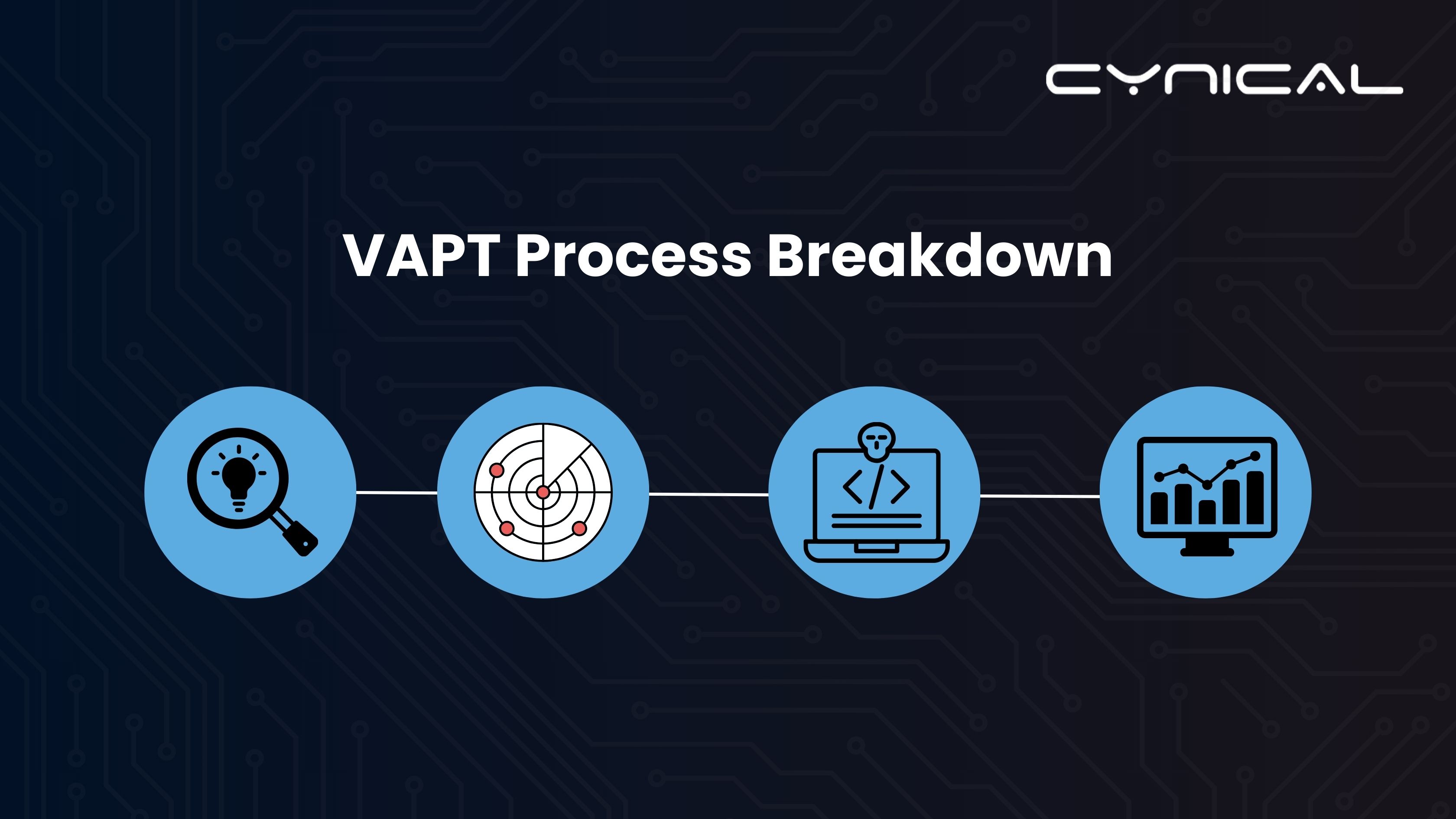
How Our VAPT Services Work
Our VAPT services follow a structured and meticulous process to uncover hidden vulnerabilities. Here’s a detailed breakdown of each step:
1. Discovery Phase
In the discovery phase, we map out your digital assets and identify potential targets. This includes:
- Cataloging all applications, networks, and servers.
- Identifying entry points and interfaces that could be vulnerable.
Tools Used: Network scanners, asset discovery tools.
2. Vulnerability Scanning
We use automated tools to scan for known vulnerabilities. This process helps in:
- Identifying outdated software, misconfigurations, and missing patches.
- Categorizing vulnerabilities based on their severity.
Example: A scan might reveal an unpatched version of WordPress susceptible to a remote code execution (RCE) vulnerability.
Tools Used: Nessus, OpenVAS, Nikto.
3. Exploitation (Penetration Testing)
In this phase, our ethical hackers attempt to exploit the identified vulnerabilities. This step verifies if the vulnerabilities can be exploited and assesses their potential impact.
Example Scenarios:
- SQL Injection: Extracting sensitive data from a database.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web pages.
- Privilege Escalation: Gaining higher-level access to the system.
Tools Used: Metasploit, Burp Suite, SQLmap.
4. Post-Exploitation Analysis
After exploiting the vulnerabilities, we analyze the extent of the compromise and document:
- The data accessed or manipulated.
- The systems impacted.
- The potential consequences if exploited by real attackers.
5. Detailed Reporting
We provide a comprehensive report detailing:
- All vulnerabilities identified.
- Steps taken during exploitation.
- Risk levels and potential impacts.
- Recommendations for remediation and mitigation.
Our reports are tailored for both technical teams and business stakeholders, ensuring everyone understands the findings and the actions required.
Real-World Case Study: SQL Injection Vulnerability
The Challenge:
A leading e-commerce company approached us to perform a VAPT of their website. During the assessment, we identified an SQL Injection vulnerability in their product search functionality.
Our Process:
- Discovery: We mapped out the search input fields and parameters.
- Scanning: Our automated scanner flagged a potential SQL Injection issue.
- Exploitation: Our penetration testers manually exploited the vulnerability to access the database and retrieve sensitive customer data.
- Reporting: We provided a detailed report highlighting the vulnerability, the steps to exploit it, and recommendations to sanitize inputs and update database queries.
The Outcome:
The company immediately applied the recommended fixes, safeguarding their customer data and preventing a potential breach.
Benefits of Choosing Our VAPT Services
- Experienced Team: Certified ethical hackers with real-world experience.
- Customized Approach: Tailored assessments based on your organization’s needs.
- Actionable Insights: Clear, concise reports with step-by-step remediation guidance.
- Ongoing Support: Post-assessment consultations to ensure vulnerabilities are properly addressed.
Conclusion: Stay One Step Ahead of Attackers
Cyber threats are continuously evolving, and your organization’s security needs to keep pace. Our VAPT services help you identify hidden vulnerabilities and secure your systems before attackers can exploit them.
Don’t wait until it’s too late — protect your business today!
