What is DDoS attack?
DDoS is an abbreviation for Distributed Denial of Service. An assault on the service or network is launched with the intent of interrupting regular functioning. Hackers bombard the victim with continual traffic, such as HTTP floods, Ping floods, fake requests, and so on.
DDoS assaults are successful because they use a large number of hacked computer systems as the source of attack traffic. Other network resources, such as PCs and Internet of Things devices, can also be used. Because the server is too busy dealing with DDoS, the computer or client network will be denied service with DDoS, the computer or client network will be denied service.
The attacker will create a malicious application and spread it across the internet, distributing it through numerous websites and email attachments.
How does DDoS attack work?
DDoS assaults are launched simultaneously from various sources, where the primary computer may interact with other attacking computers. After several attacks, the server will be overburdened, consuming system resources such as CPU, memory, and network bandwidth, causing overall operations to be exceedingly sluggish.
If a compromised computer visits malicious application websites and opens the malicious email, malware will be installed without the owner realizing it. Their PC has now been enlisted in a DDoS assault army. This is referred to as a botnet.
A botnet is an army of infected computers, the main computer of which can control other computers.
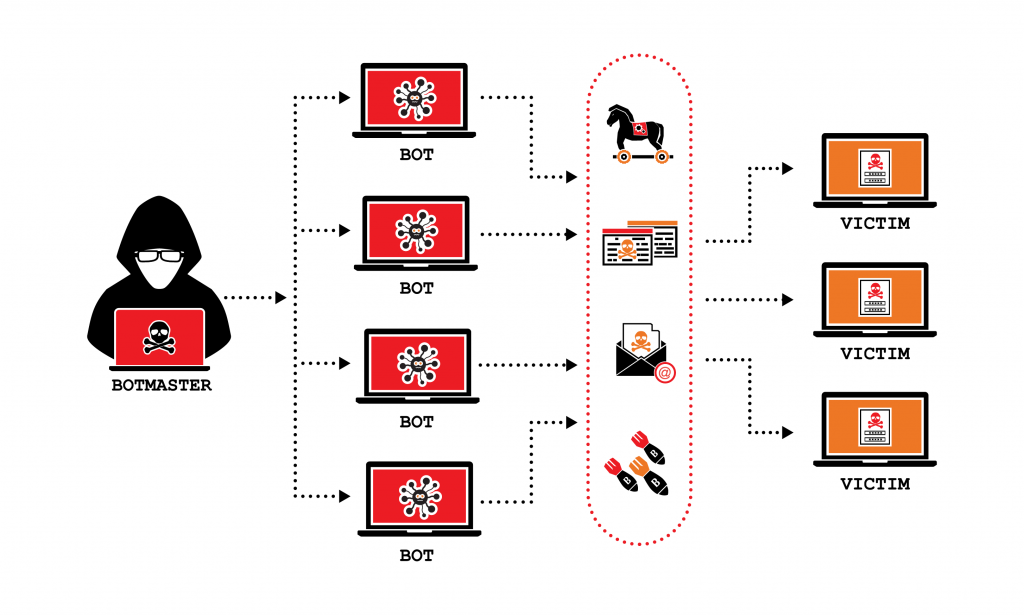
DDoS attack happens for:
- Financial Reasons
- Political Reasons
- Fun/Experiment
How long do these attacks last?
The duration of a DDoS assault varies. Some occur over a lengthy period of time, while others endure only a short time.
- Long Term Attacks: Attacks that last for hours or days are considered as long-term attacks.
- Burst Attacks: Attacks that last only for a minute or a few seconds.
How to identify a DDoS Attack?
When a website or service suddenly slows down or becomes inaccessible, this is the most visible indicator of a DDoS assault. Similar performance concerns, such as legitimate traffic surges, might arise for a variety of reasons and should typically be studied further.
Some of these clear symptoms of a DDoS assault can be detected using traffic analysis tools. A strange volume of traffic originating from a single IP address or IP range, or abnormal traffic patterns such as odd-hour increases throughout the day, are some telltale symptoms of a DDoS assault. Other particular symptoms of DDoS assaults vary according to the type of attack.
