- February 6, 2025
- Posted by: Bikash Sharma
- Category: Awareness, Business plans

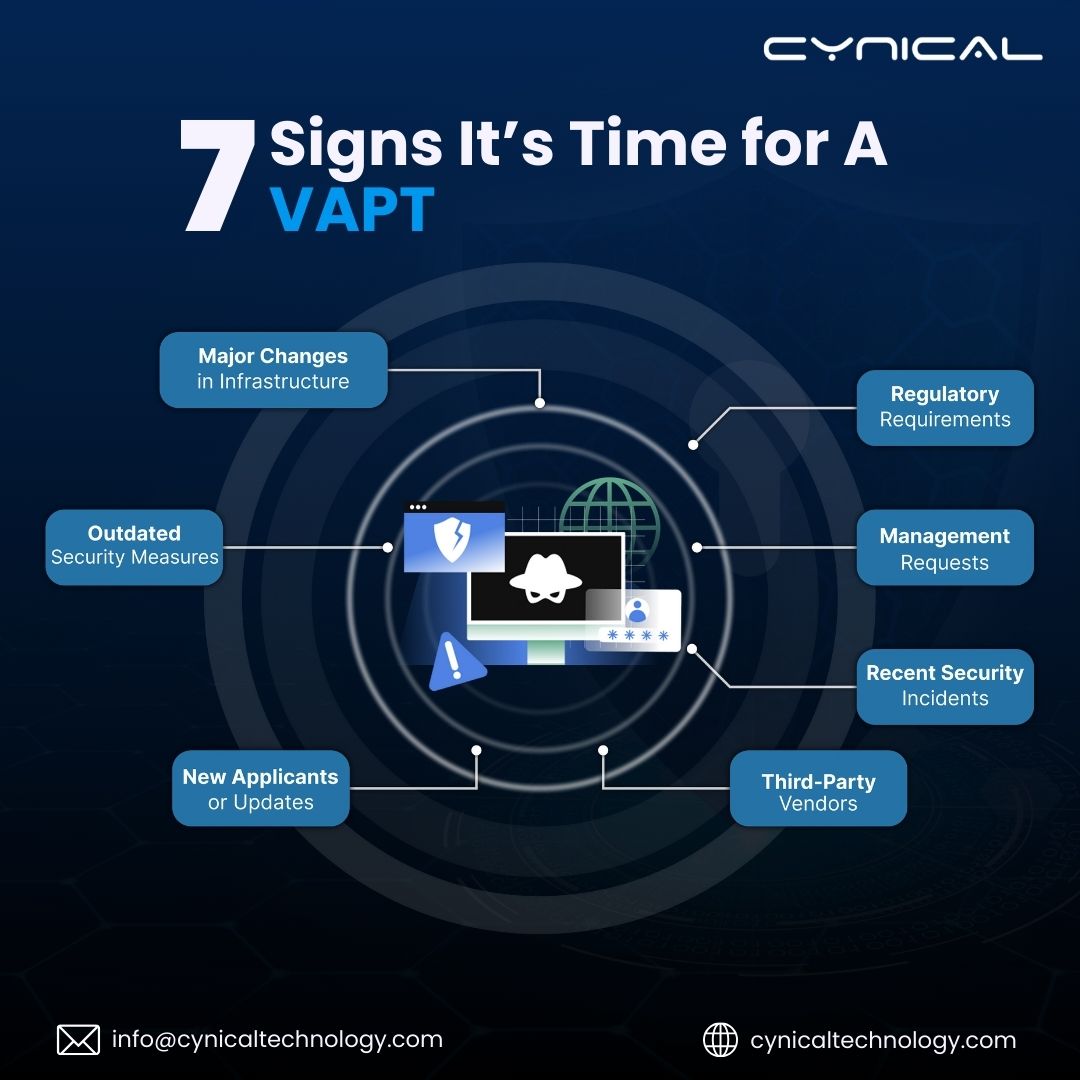
7 Signs It’s Time for a VAPT
 In an era where cyberattacks are at an all-time high, businesses must take a proactive approach to cybersecurity. Ignoring vulnerabilities in your IT infrastructure can result in severe financial, legal, and reputational damages. One of the most effective ways to strengthen your cybersecurity defenses is through Vulnerability Assessment and Penetration Testing (VAPT).
In an era where cyberattacks are at an all-time high, businesses must take a proactive approach to cybersecurity. Ignoring vulnerabilities in your IT infrastructure can result in severe financial, legal, and reputational damages. One of the most effective ways to strengthen your cybersecurity defenses is through Vulnerability Assessment and Penetration Testing (VAPT).
But how do you know when it’s time for a VAPT assessment? Here are seven critical signs that indicate your organization should immediately prioritize security testing.
1. Major Changes in IT Infrastructure
Every time you make significant changes to your IT infrastructure—whether it’s migrating to the cloud, upgrading software, integrating new technologies, or restructuring your network—you introduce potential security gaps.
For example:
- A company moving its operations to cloud-based servers may unknowingly expose sensitive data due to misconfigured permissions.
- Businesses upgrading their ERP systems might introduce vulnerabilities that cybercriminals can exploit.
- Adding new network devices without properly securing them can create entry points for hackers.
A VAPT assessment ensures that these new changes do not introduce security risks by identifying vulnerabilities before attackers do.
2. Regulatory & Compliance Requirements
If your business operates in an industry that handles sensitive data—such as finance, healthcare, e-commerce, or IT—you are likely required to comply with cybersecurity regulations like:
✅ GDPR (General Data Protection Regulation) – Protects customer data in the EU.
✅ PCI DSS (Payment Card Industry Data Security Standard) – Mandates secure handling of payment information.
✅ HIPAA (Health Insurance Portability and Accountability Act) – Ensures protection of patient healthcare data.
✅ ISO 27001 – International standard for information security management.
Failing to comply with these regulations can lead to heavy penalties, legal actions, and loss of customer trust. A regular VAPT helps you stay compliant and prevent security lapses before they turn into legal liabilities.
3. Outdated Security Measures & Systems
Hackers are always finding new attack techniques, and if your security measures haven’t been updated in a long time, you’re at risk.
Common signs of outdated security include:
- Using old software versions that no longer receive security updates.
- Weak firewall rules or improper access controls.
- No multi-factor authentication (MFA) for critical systems.
- Lack of end-to-end encryption for sensitive data.
Cybercriminals target businesses with outdated security measures because they are easier to exploit. A VAPT assessment helps you identify outdated security practices and replace them with modern, robust solutions.
4. Management Requests & Cyber Risk Assessments
Your company’s leadership team may request a security audit as part of a business risk assessment or internal policy review. Many organizations conduct VAPT tests to:
- Gain investor confidence by demonstrating strong security.
- Ensure business continuity in case of cyber threats.
- Protect intellectual property and sensitive corporate data.
A well-documented VAPT report not only helps in identifying risks but also serves as proof of due diligence to stakeholders, customers, and regulatory bodies.
5. Recent Security Incidents or Breaches
If your business has experienced any of the following incidents, it’s an urgent sign that you need a VAPT assessment:
⚠️ Data breach – Customer or employee information has been leaked.
⚠️ Phishing attack – Employees have fallen for scam emails, exposing login credentials.
⚠️ Ransomware attack – Your company has been locked out of its systems due to malware.
⚠️ DDoS attack – Your website or application has been overwhelmed with fake traffic, causing downtime.
Even if you’ve resolved the issue, there might still be hidden backdoors, misconfigurations, or security weaknesses. A VAPT test helps identify residual threats and ensures that similar attacks won’t happen again.
6. Onboarding New Employees or Third-Party Integrations
Many cyberattacks happen due to human error, often from new employees or third-party vendors who might unknowingly introduce security risks.
⚠️ New Employees:
- They might reuse weak passwords across multiple accounts.
- They could fall for phishing emails, compromising company credentials.
- They might misconfigure security settings, exposing sensitive data.
⚠️ Third-Party Vendors:
- If your business integrates with third-party SaaS platforms, their security vulnerabilities could impact you.
- Supply chain attacks have become a major cyber threat, where hackers compromise vendors to infiltrate larger organizations.
A VAPT assessment ensures that your security policies cover new employees and third-party integrations, reducing the risk of external threats.
7. Working with Third-Party Vendors & Supply Chain Risks
Businesses today rely on third-party vendors, cloud services, and external software providers. However, if their security is weak, your business is also at risk.
🔍 Example of a supply chain attack:
In 2020, the SolarWinds attack exposed the sensitive data of Microsoft, U.S. Government agencies, and major Fortune 500 companies. Hackers infiltrated SolarWinds’ software updates, affecting over 18,000 customers worldwide.
🔐 How can you protect your business?
✔️ Conduct a VAPT on third-party integrations to check for weaknesses.
✔️ Ensure zero-trust security policies are in place for external vendors.
✔️ Use secure APIs and encrypted connections when integrating third-party services.
By proactively conducting a VAPT assessment, you can mitigate supply chain risks before they turn into full-blown cyberattacks.
Final Thoughts: Don’t Wait Until It’s Too Late!
Cyber threats are constantly evolving, and businesses that fail to proactively assess their vulnerabilities are easy targets for attackers. Waiting until a breach happens is NOT an option—prevention is always better than cure.
🔹 VAPT helps you:
✅ Identify security weaknesses before hackers do.
✅ Stay compliant with industry regulations.
✅ Protect your business, customers, and stakeholders from data breaches.
✅ Strengthen your cybersecurity strategy for long-term resilience.
At Cynical Technology, we specialize in Vulnerability Assessment & Penetration Testing (VAPT) to help businesses fortify their cybersecurity defenses.
🚀 Secure your business today! Contact us at info@cynicaltechnology.com or visit cynicaltechnology.com to schedule a VAPT consultation.
🔐 Stay Secure. Stay Ahead.
